I hate companies that make users think they’re getting something for free but then have these hidden functions that report back to the mother-ship what users are doing with them. WordPress’s parent company, Automattic, doesn’t have the best reputation as of late (check out the deal they made to sell your data to OpenAI). Just now I was prompted to “Verify your admin email address is still correct” while logging in. That seems innocent enough – and even mildly HELPFUL… but if you knew what Automattic was REEEAAAALLY doing, you would think differently. When you click that cute little blue button to “confirm” your information is correct it’s not just saving your email address locally (you DO host WordPress yourself, right?).
119 6 veth119i0-OUT 11/Apr/2024:18:06:40 -0400 policy DROP: IN=fwbr119i0 OUT=fwbr119i0 PHYSIN=veth119i0 PHYSOUT=fwln119i0 MAC=bc:24:11:60:5d:f6:22:e5:10:fa:b2:af:08:00 SRC=172.16.13.32 DST=198.143.164.251 LEN=60 TOS=0x00 PREC=0x00 TTL=64 ID=61509 DF PROTO=TCP SPT=46840 DPT=443 SEQ=1268854965 ACK=0 WINDOW=62720 SYN Above we see the web server being denied a TCP connection to an HTTPS endpoint (thank you, outbound firewall). Let’s reverse lookup that IP to see who it belongs to…
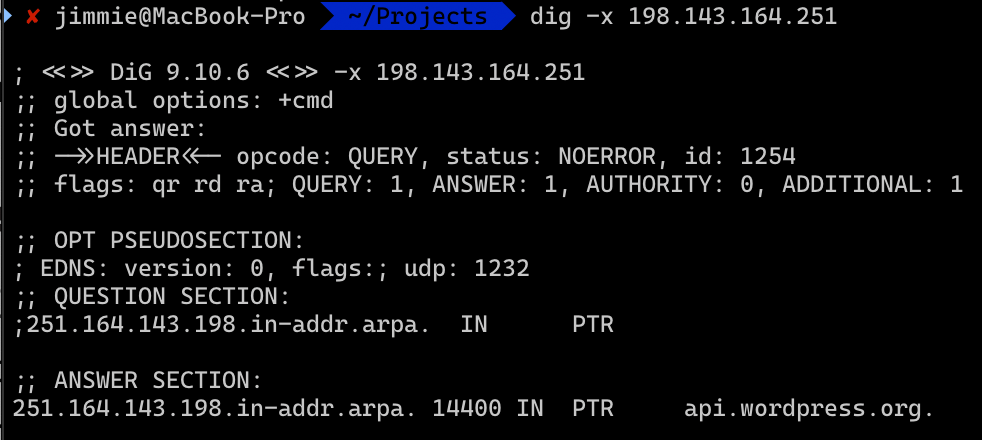
WordPress, you sneaky little pricks! What a clever way to hoover up user data! We can only assume they were going to guzzle that email address and who knows what else.
In order to keep your data safe from these dilberts, I’d suggest hosting WordPress in a manner where you can control both INBOUND and OUTBOUND traffic flows. I do this with the built-in firewall of a piece of software called Proxmox – an open source virtualization platform.
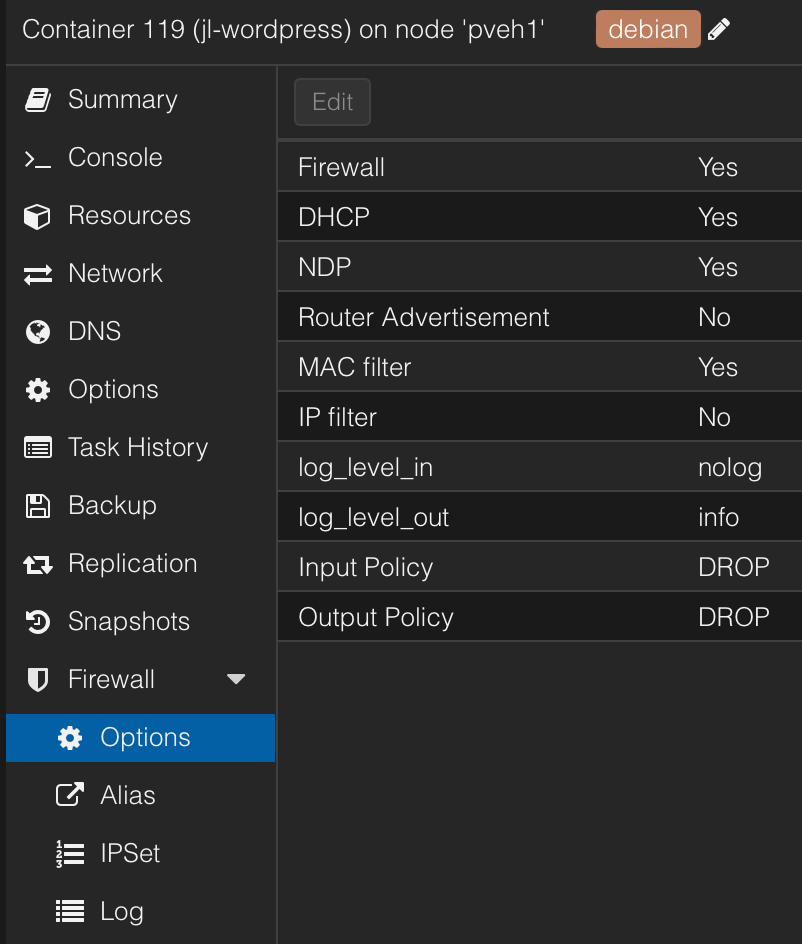
When I spin up a Linux container, I like to set some VERY strict rules for how it can access the network. In my case, both Input and Output policy for the firewall are set to DROP. This allows me to be very granular when permitting only the traffic necessary.
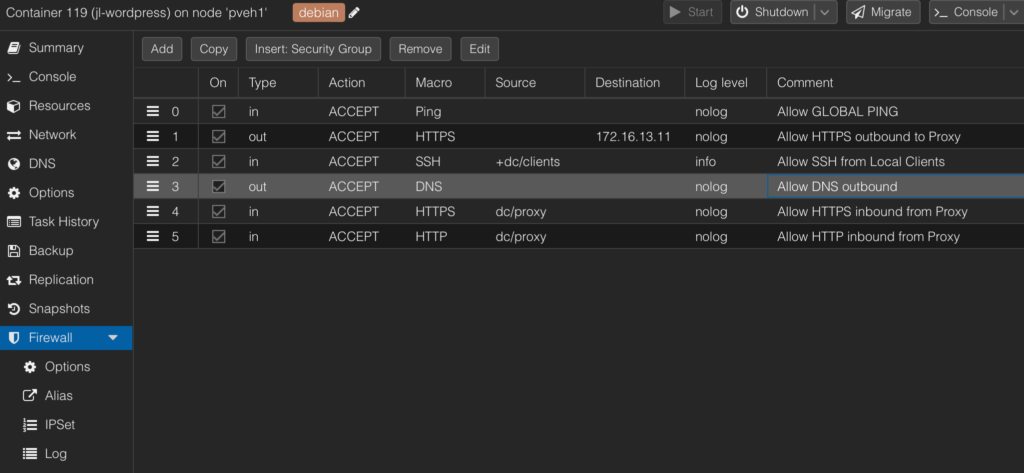
For this container I allow only outbound access to perform DNS lookups and to my local proxy service. Inbound HTTP and HTTPS are only permitted from the Proxy. Anything else not explicitly defined hits those default drop rules. When it’s time to perform software updates, I stop the web server in the container before temporarily toggling the Output Policy to allow traffic so that WordPress doesn’t sneakily send anything while my guard is down.
I hope this has been enlightening!